| atk > documentation > help > logs | Last update: 2004/11/02 by Marc Ruef |
Logs
Logging is a very important mechanism for every software. Because this is a possible way to get verbose information on how the application handles different things. Especially in problem cases where debugging is needed could the logging bring the brightness.
The log frame can be reached by clicking on the log icon or Anylsis/Logs on the main frame. After this a new resizable frame is opened. Usually the most actual log file in the default log directory is opened. The default log directory is /logs. All ATK log files are saved as comma seperated value files with the ending .log

The list view element is the central part of the log frame. Here is the log data shown. Every log entry is shown in a different line. And the data fields of such an entry is shown in a seperate column. These are:
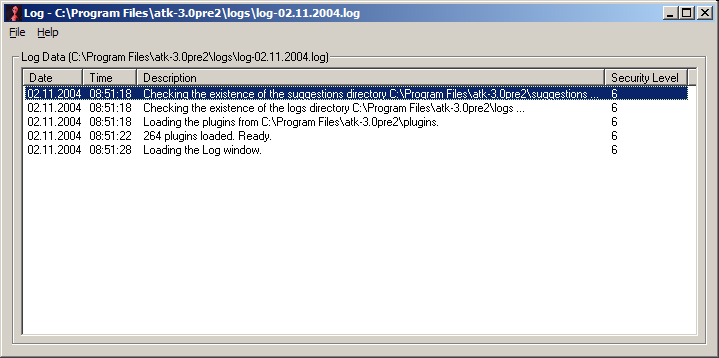
If you double click a log entry, a message box will show the data. This is useful if the log entry is unreadable in the listview.
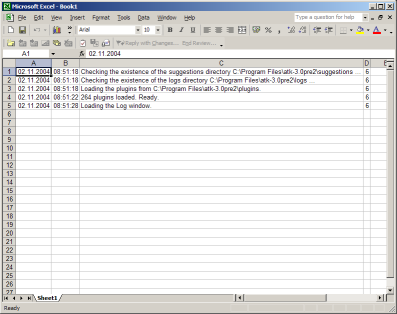
Because the log files are usual ASCII files you are able to view them with your favorite text editor. Opening a log file with an utility as like notepad.exe shows you the column seperated values:
02.11.2004;08:51:18;Checking the existence of the suggestions directory C:\Program Files\atk-3.0pre2\suggestions ...;6As in the log frame in the first column the date, in the second the time, in the third the description and in the fourth the security level can be found. It is very easy to import such a file into Microsoft Excel for example. So further analysis or computation can be done. Use the usual way for importing external data.
02.11.2004;08:51:18;Checking the existence of the logs directory C:\Program Files\atk-3.0pre2\logs ...;6
02.11.2004;08:51:18;Loading the plugins from C:\Program Files\atk-3.0pre2\plugins.;6
02.11.2004;08:51:22;264 plugins loaded. Ready.;6
02.11.2004;08:51:28;Loading the Log window.;6
Feel free to write your own application that can handle, analyze, convert or export ATK log files. Log analysis is very important in IT security - and especially in security auditing and intrusion detection. But be aware that such a log file may contain sensitive data as like paths, target hosts and found vulnerabilities. That is why log files should kept secret and save. Only trusted users access to them should be granted.