| atk > documentation > help > attack response | Last update: 2004/11/06 by Marc Ruef |
Attack Response
Transparency is one of the main goals of the Attack Tool Kit project. Transparency means that it is possible to see whatever is going on and this whenever it is wanted. The Attack Response is another frame that provides such a transparency during and after an attack.
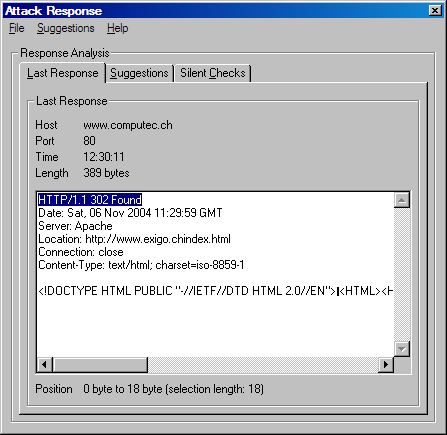
The Attack Response can be opened by clicking on the response icon on the main frame. Another sub frames opens. As you can see the last response is printed in a textbox. So you are able to make a further analysis of this response. False positives or false negatives can be found or data for further attacks can be detected.

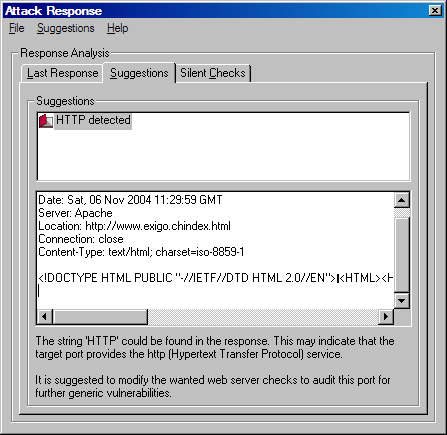
In the Attack Response different tabs are given. The suggestions tab makes an indipendent and deep analysis of the loaded response. Afterwards the software provides a suggestion what the next steps in the running security audit or penetration test may be. You are running for example a specific buffer overflow check for ftp servers on an unpopular port (e.g. 721). The attack is not successfull and you do not really know why. The suggestion frame may be able to detect that a web server is running on the selected port. This would be a good reason why the ftp audit was not able to be successfull. The suggestion might be to ignore ftp checks and load the available http checks to test the found web server.