spread project advanced covert file distribution |
| Introduction | News | Client | Server | Documentation | Contact |
| The security of internal hosts heavily relies on the integrity of the hosts. For example the personal workstation of an employee by a company gets an important part within the security of itself, the whole company network and all other networks. If an external or internal attacker (in this case the user of the workstation) is able to compromise the security of the workstation, she might be able to gain elevated privileges. Therefore the administrators of the company try to prevent attackers to load their own attack software or exploiting code on the workstations. An important part in such kind of multi-layered security is a firewall gateway which shall prevent users from downloading software to the host. The firewall tries to identify unwanted file extensions (e.g. exe and zip) or potentially dangerous contents (e.g. by MIME types or file streams). If an user tries to download such a file, the access attempt is prohibited. There are different ways to test the security of an environment. A local security analysis, which tries to determine the security level of the protected environment from different points of view, became more and more important. Especially which solutions like Citrix where multiple users share a virtual workstation (served by a server). An important goal of such local penetration tests is the download of potentially dangerous and usually for further testing usefull software. The spread project provides research and solutions for this tasks. The spread software shall help to download prohobited file types by using different approaches of security circumvention. The concept is based on a traditional client/server architecture. The spread server provides the files which shall be downloaded. Those are converted into a specific format which is not understood nor prevented by security solutions (e.g. filtering software). An example of such an encoding is shown below (the first bytes of cmd.exe):
The converted data is downloaded from the spread server and put into the spread client. The clients are available in different version (e.g. a common EXE file or an embedded VBA within a Word document). After downloading the converted data the spread client is able to re-code the original software and save the file. Thus, it is possible to download and use files which might not be downloadable within the usual way. 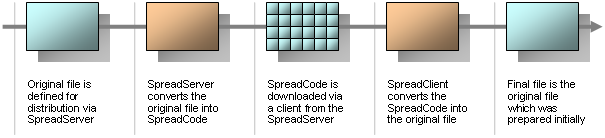 |
| © 2007-2024 by Marc Ruef |